Last year was an eventful one for the IT-security field. There were a lot of incidents, starting with global vulnerabilities to showdowns with local cybercriminals. So, as way of looking back we decided to pull together ten of the best security related tweets.
Did we miss one? Let us know in the comments below!
1. Pumpwater – In March a cyber-criminal who acted on behalf of ‘Pump Water Reboot’ hacker group started a series of DDoS attacks on a bunch of Russian web services — from popular online communities to banks. Each victim was asked to pay $1000 ransom to stop the attack.
In this particular post, the criminal threatened a Russian banker, Oleg Tinkov, founder of Tinkoff Credit Systems which is online specialized bank.
@olegtinkov На ваш сайт ведется DDoS – атака. Мы предлагаем решение этой проблемы. Атака прекратится если Вы готовы заплатить 1 000$.
— Pump Water (@PumpWaterReboot) March 24, 2014
(Translation: Your site is under DDoS attack. We offer a solution to this problem. The attack will stop if you are willing to pay $ 1,000.)
It didn’t take long for things to happen: by the summer, the criminal was caught by police and was sentenced to 2.5 years of probation and a fine of 12 million rubles (about $400,000 at that moment).
2. Heartbleed — The vulnerability that threatened over two thirds of the internet. If you’re unsure what the Heartbleed bug is, you can get up to date on our blog post here. However, if you’re after a succinct and precise explanation, look no further than XKCD:
Heartbleed http://t.co/wxVnw6YK6Q http://t.co/j1iYb4DC7l pic.twitter.com/ekr3nFr1oW
— XKCD Comic (@xkcdComic) April 9, 2014
Despite all the press attention that the bug received (it even got it’s own logo) there’s still tens of thousands of compromised servers out there.
3. The CIA join Twitter – In our opinion, the best tweet of the year was goes to (believe it or not) the CIA. It just goes to show that even brands such as this can use social media well:
We can neither confirm nor deny that this is our first tweet.
— CIA (@CIA) June 6, 2014
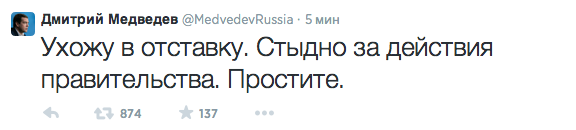
4. Russian PM Twitter – In mid-August there was that sooner or later happens with almost every modern politics. Someone hacked Twitter account of Russia’s Prime Minister Dmitry Medvedev and made a lot fun of it.
(translation from Russian: I resign. I am ashamed of the government’s actions. I’m sorry.)
At the same time other accounts of Medvedev were also hacked, which led to private photos and correspondence from Medvedev’s being leaked. All these posts have subsequently been removed and the whereabouts of the hackers remains unknown.
5. Celebrity leaks – Two weeks later there was another leak, this time on a much larger scale was to happen. Leaked nude images of celebrities was about to cause a social media storm.
Someone apparently has hacked into Jennifer Lawrence's iCloud account and is releasing pictures from her camera roll pic.twitter.com/l0ua4bejIc
— Háider (@YahoodiSaazish) August 31, 2014
Subsequently nick-named “The Fappening” by Reddit users, there was huge publicity around the pictures, but not just because of the nature of the images. Apple’s iCloud services, where the pictures had been stored took a lot of flack for their encryption. Apple would later announce full encryption as part of iOS 8.
6. Shell-shocked – Autumn was especially eventful. In September a new vulnerability was found in Bash shell. Popularly known as Bashdoor or Shellshock, it was second time within one year where millions of computers (mostly servers) were compromised. The man who has discovered this bug didn’t post anything in his Twitter immediately. However, later he posted that the bug was not actually that new at all:
Shellshock was actually introduced in bash-1.03 (1989, 25y ago), not 1.13 as Chet, I and others have said earlier (http://t.co/LC5TEqpqkx)
— Stephane Chazelas (@SChazelas) October 4, 2014
Similar to Heartbleed, Shellshock will haunt IT security for years to come.
7. BADUSB – A couple of week later the world found out about another global threat: in early October two researchers announced that every USB-device on the planet is fundamentally vulnerable. For some reasons, these guys didn’t talk about this it, but we did:
BadUSB research: "You can’t trust anything you plug into your PC, not even a flash drive" https://t.co/kOkdrw8dEZ pic.twitter.com/ANYpF01EY6
— Eugene Kaspersky (@e_kaspersky) October 3, 2014
It is still unclear what we should do globally to protect ourselves from this bug. There is only one known good practice: do not use untrusted USB-devices and that even includes mice and keyboards.
8. Dropbox hacked? – In mid-October there was another leak, this time victims were Dropbox users. Company representatives promptly declared that service wasn’t hacked and leaked data was collected in some other ways.
Reports claiming we’ve been hacked aren’t true. Your stuff is safe. More info on our blog: http://t.co/vI6sfNjC4Z
— Dropbox Support (@dropbox_support) October 14, 2014
9. Introducing Digits – The end of October was marked by event that (sadly) didn’t receive enough attention. Twitter announced plans to replace passwords with another, more advanced authentication system. And not only passwords for the accounts of its own users: Twitter offers third-party developers the ability to use the system as well.
There were many attempts to get rid of passwords and, as we have seen, nobody has been able to achieve this so far. But it is possible that Twitter will succeed and in a few years we will finally stop using this old good authentication method.
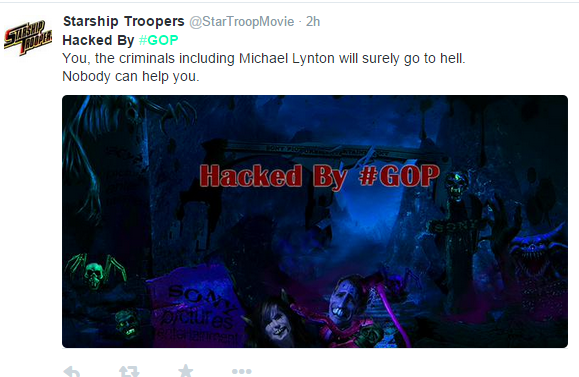
10. Sony – As for passwords: never store it in unencrypted file on your PC. Otherwise, you may well face the same thing that happened to Sony Pictures. The, now infamous hack, was preluded by the hacking of the Starship Troopers twitter account:
The aftermath was swift and brutal with everything from emails to movies being dumped on file-sharing sites across the world. Sony have been widely criticised by IT professionals for poor security pratices (yes, even keeping passwords in plain text files.) You can learn more about what happened with Sony in our blog post.
 bashdoor
bashdoor

 Tips
Tips